Linux Networking: Open Ports / Listening Services
Understanding the open ports and listening services on your Linux system is a critical part of network management and security. Open ports can reveal which applications are actively communicating or awaiting connections, but they can also expose your system to potential vulnerabilities if left unchecked.
Introduction
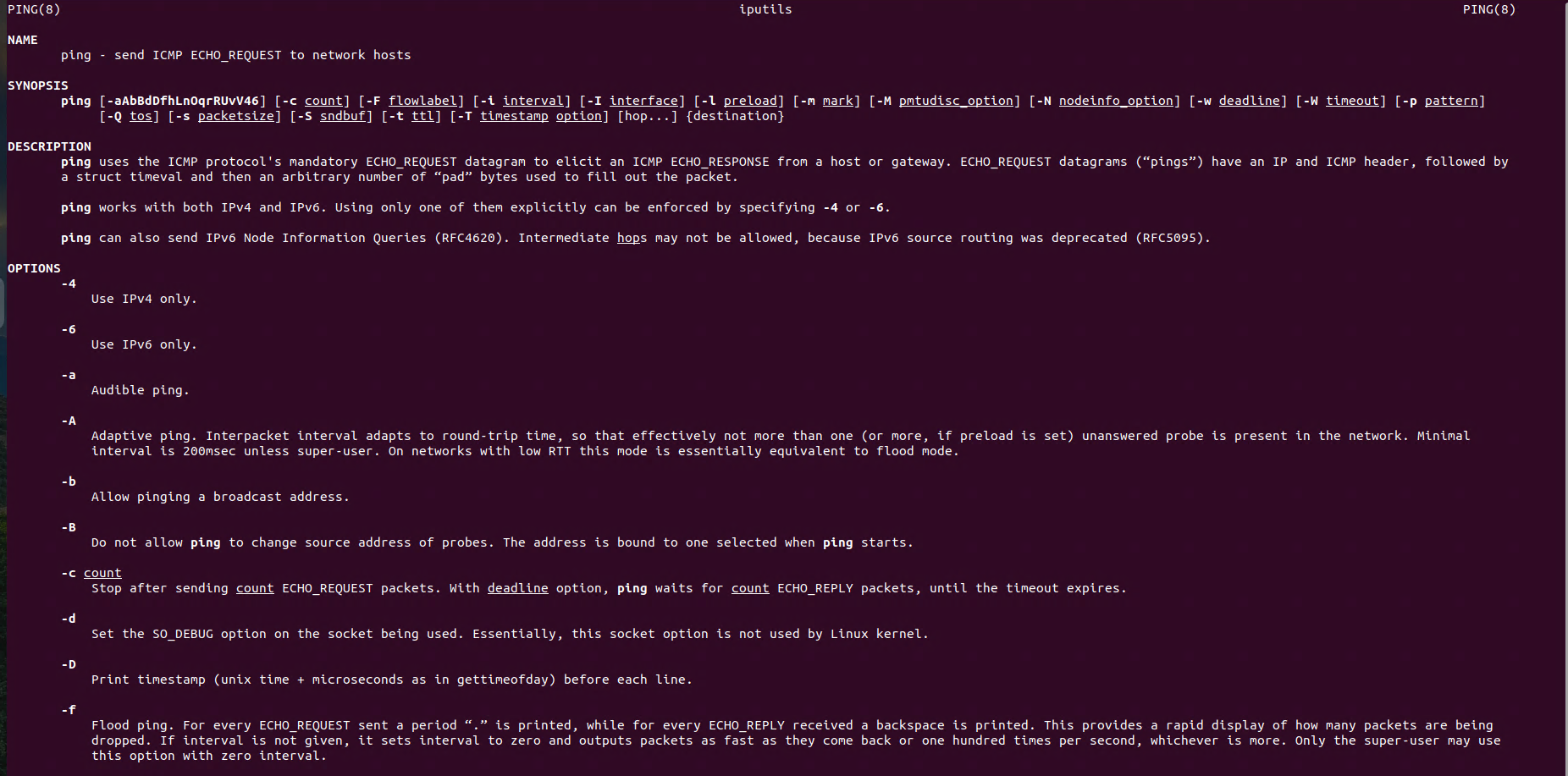
The netstat command is a powerful network utility available on Linux that provides a variety of network-related information. With this tool you are able to display open ports and listening services on Linux Systems. The netstat command is essential for network administrators and users who need to monitor and troubleshoot network connections.
With the right tools and commands, you can quickly identify open ports and their associated processes. Whether you’re troubleshooting network connectivity, optimizing system performance, or strengthening your security posture, this information is invaluable.
In this article, we’ll explore how to display open ports and listening services using powerful Linux commands like netstat, ss, and lsof, helping you gain better control over your system’s network
Display Active Connections
netstatInformation from manaul for netstat: This program is mostly obsolete. Replacement for netstat is ss. Replacement for netstat -r is ip route. Replacement for netstat -i is ip -s link. Replacement for netstat -g is ip maddr.
Display Open Ports
netstat -l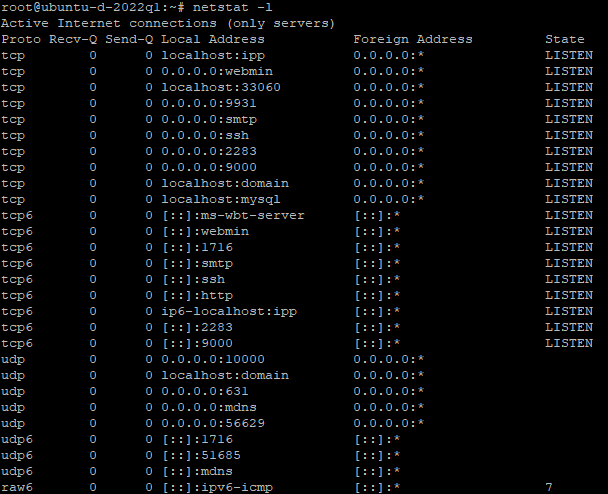
This command lists all listening ports. For a detailed view, including TCP and UDP ports, use:
netstat -ltu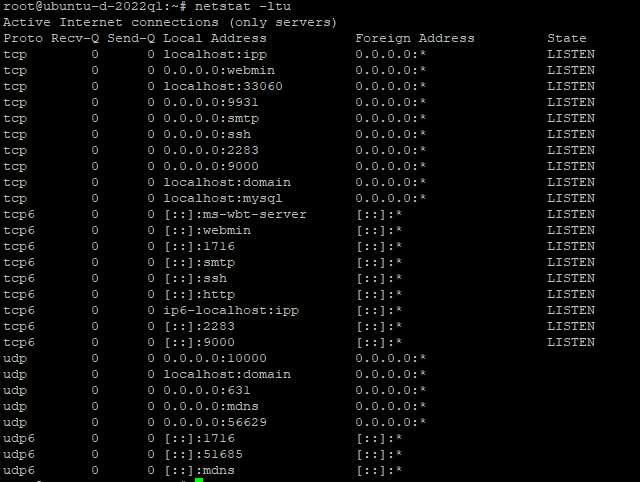
Viewing Listening Services
netstat -tuln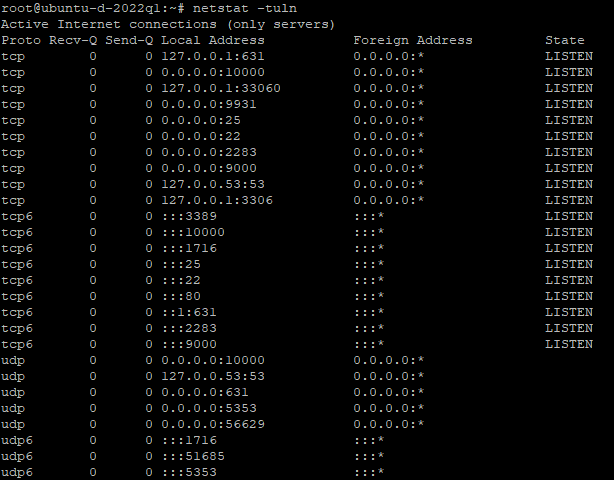
This command lists all the listening services along with their respective ports in numeric form.
Using lsof -i :PORT to Identify Which Process Is Listening on a Port
Another powerful tool for network diagnostics on Linux is the lsof command. It can be used to display which process is listening on a specific port — extremely helpful when a port is unexpectedly in use or during service troubleshooting.
The syntax is simple:
sudo lsof -i :PORTThis command will list any process that is actively using the specified port, including protocol type, process ID (PID), user, and the program name.
Why it’s useful
- Troubleshooting “Address already in use” errors during service installation
- Verifying whether a service is actively listening on the expected port
- Detecting unauthorized or unknown applications using open ports
Examples
Check who is using HTTP port (80):
sudo lsof -i :80Output:
COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME
docker-pr 1651 root 7u IPv4 25402 0t0 TCP *:http (LISTEN)
docker-pr 1671 root 7u IPv6 25403 0t0 TCP *:http (LISTEN)Check HTTPS port (443):
sudo lsof -i :443Verifies if secure web services are properly listening on port 443.
Check SSH port (22):
sudo lsof -i :22Output:
COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME
sshd 796 root 5u IPv4 20897 0t0 TCP *:ssh (LISTEN)
sshd 796 root 6u IPv6 20899 0t0 TCP *:ssh (LISTEN)
sshd 682911 root 4u IPv4 5874667 0t0 TCP 192.168.20.110:ssh->192.168.20.113:50068 (ESTABLISHED)Used to confirm that the SSH daemon is running and accessible.