FortiGate Log Management
FortiGate Logging and general logging is a crucial aspect of network security and monitoring, allowing administrators to track activities, diagnose issues, and ensure compliance. Fortinet FortiGate provides extensive logging capabilities, capturing detailed information about network traffic, security threats, and system events. This guide explores FortiGate logging, covering log types, severity levels, local and remote logging, best practices, and log management techniques. By implementing effective logging strategies, organizations can enhance network visibility, improve threat detection, and optimize performance.
Log Basics
As traffic moves through the FortiGate firewall and into the network, FortiGate actively scans it and takes action based on the firewall policies. During this process, the firewall records activity and saves relevant information in a log message, which is then stored in a log file.
Logs play a crucial role in monitoring network traffic, identifying issues, and improving security. They also help fine-tune network defenses. To ensure an effective logging system, accurate date and time settings are essential. Therefore, using a Network Time Protocol (NTP) server is highly recommended.
Log Workflow
FortiGate logs provide crucial insights into network activity, security events, and system performance. The logging process follows a defined workflow:
- Event Occurrence: An event is triggered based on user activity, security policies, or system changes.
- Log Generation: The FortiGate system categorizes and formats the event into a log entry.
- Log Storage and Forwarding: Logs are either stored locally (flash memory or hard drive) or sent to remote log servers such as FortiAnalyzer, FortiManager, or Syslog.
- Log Analysis and Reporting: Administrators can view, search, and analyze logs to detect anomalies, troubleshoot issues, and generate reports.
Log Types and Subtypes
FortiGate logs are categorized into different types and subtypes:
- Traffic Logs: Capture network traffic details, including source/destination IP, protocol, and port.
- Event Logs: Record system activities such as admin logins, configuration changes, and firewall policy updates.
- Security Logs: Contain threat intelligence from features like IPS, antivirus, web filtering, and application control.
| Traffic | Event | Security |
|---|---|---|
| Forward | Endpoint Control | Application Control |
| Local | High Availability | Antivirus |
| Sniffer | System | Data Leak Prevention (DLP) |
| User | Anti-Spam | |
| Router | Web Filter | |
| VPN (Virtual Private Network) | Intrusion Prevention System (IPS) | |
| WAD (FortiOS Webproxy Process) | Anomaly (DoS-Policy) | |
| Wireless | Web Application Firewall (WAF) |
Log Severity Levels (0-7)
FortiGate assigns severity levels to logs based on their impact:
- 0 – Emergency: System is unusable.
- 1 – Alert: Immediate action required.
- 2 – Critical: Critical conditions detected.
- 3 – Error: Error conditions encountered.
- 4 – Warning: Potential issues or security concerns.
- 5 – Notification: Normal but significant events.
- 6 – Information: General informational messages.
- 7 – Debug: Detailed debug information for troubleshooting.
0 = high importance / 6 = low importance
Log Message Structure
Each FortiGate log message comprises two primary components:
- Log Header: Includes metadata such as timestamp, log ID, severity, and device details.
- Log Body: Contains detailed event information, including source, destination, and specific actions taken.
Effect of Logging on Performance
More logs = more CPU, memory, and disk space!
Extensive logging can impact FortiGate performance by consuming CPU, memory, and storage.
- Logging in Security Fabric: When you integrate Fortinet’s Security Fabric, the system centrally collects and processes logs, which helps reduce the load on individual devices.
- Optimizing Logging: To mitigate performance issues, administrators should enable only necessary logs, configure log rotation, and use external log storage solutions.
From the FortiGate CLI, you can enable performance statistics logging for remote logging devices such as FOrtiAnalyzer and Syslogto occur every 1-15 minuts. This is not possible for local disk logging or FortiCloud.
config system global
set sys-perf-log-interval <number from 0-15>
endBest Practices for Log Management
- Create a log management plan:
- What activities do you want and need logged?
- Backup solution in the event a faulure
- Archiving of logs (FortiAnalyzer can help)
- Utilize remote logging solutions to offload storage from FortiGate.
- Regularly audit logs for security and compliance.
General logging best practices:
- Enable log rotation to prevent storage overflow
- Use structured log retention policies.
Local Logging
To store logs locally on FortiGate you must enable disk logging. With disk logging enabled , the report daemon collects statistics used for historical FortiView from disk. By default, logs older than seven days are automatically deleted. from the disk. You can change it on this way:
fgt-remote1 # config log memory global-setting
fgt-remote1 (global-setting) # get
max-size : 65536
full-first-warning-threshold: 75
full-second-warning-threshold: 90
full-final-warning-threshold: 95
Flash Memory
FortiGate devices with onboard flash memory can store logs locally (not recommended), but the storage capacity is limited.
- Constant rewrites can reduce the lifteime and efficiency of the memory
- Logging disabled by default
- Not recommended for logging, should use external logging device instead
Hard Drive
Some FortiGate models include a hard drive for extended log storage. Hard drives allow for longer retention periods and are useful for local log analysis before offloading logs to a remote server.
- FortiGate devices that have a hard drive store logs in a SQL database
- Reports retrieve data from the SQL database.
Remote Logging
FortiAnalyzer
FortiAnalyzer provides centralized log collection, storage, and analysis with advanced reporting and event correlation.
FortiManager
FortiManager integrates logging with network management, allowing administrators to monitor configurations, policies, and logs in one platform.
Syslog
Syslog servers collect logs from multiple devices for long-term storage, analysis, and integration with third-party SIEM solutions.
FortiCloud
FortiCloud offers cloud-based log storage and analysis, reducing on-premises storage needs while providing accessibility from anywhere.
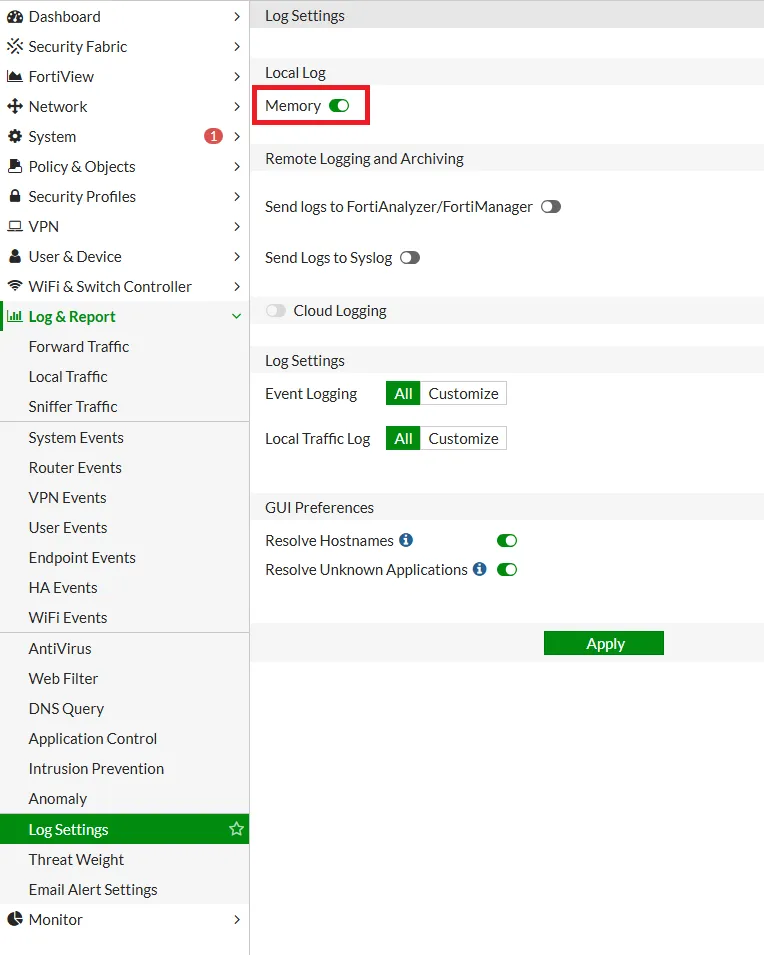
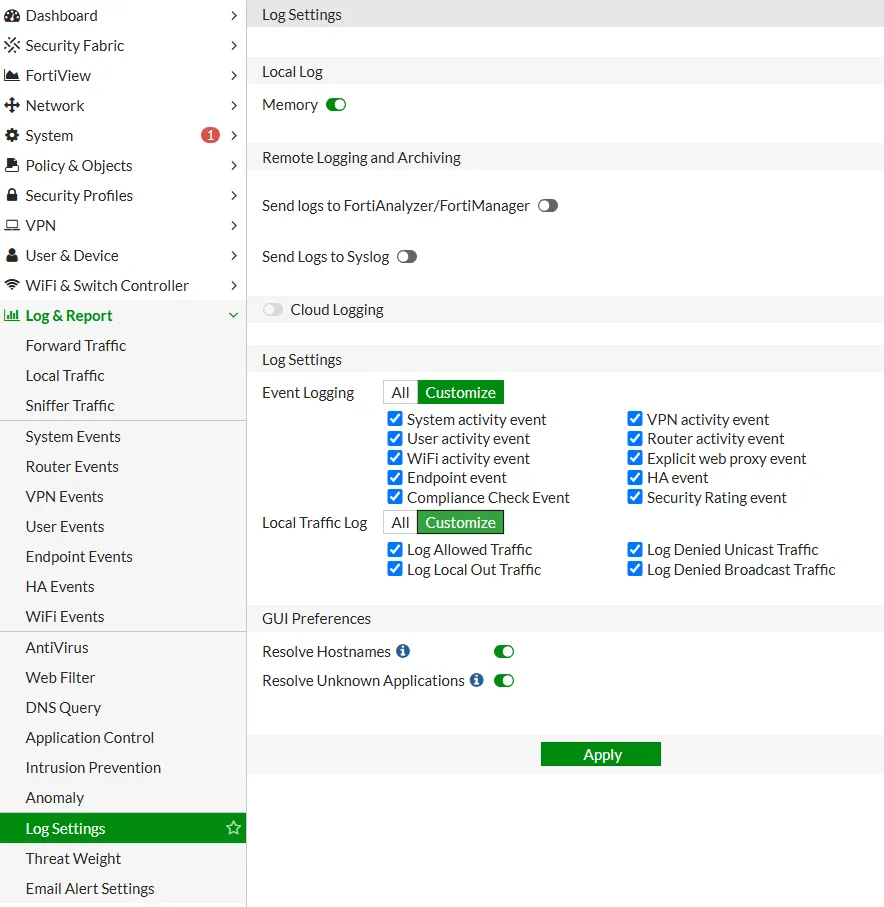
Log Settings
Administrators can configure logging settings under Log & Report > Log Settings in the FortiGate GUI. Key configurations include:
- Enabling/disabling logs for specific events
- Setting log levels for different services
- Choosing log storage locations (local vs. remote)
- Configuring log retention and rotation policies
Viewing, Searching, and Monitoring Logs
Logs can be accessed via:
- GUI: Under Log & Report, logs are categorized for easy viewing.
- CLI: Use
execute log displaycommand. - FortiAnalyzer/FortiManager: Provides advanced search and filtering capabilities.
fgt-remote1 # execute log display
0 logs found.
0 logs returned.Generate test log message:
diagnose log test
generating a system event message with level - warning
generating an infected virus message with level - warning
generating a blocked virus message with level - warning
generating a URL block message with level - warning
generating a DLP message with level - warning
generating an IPS log message
generating an anomaly log message
generating an application control IM message with level - information
generating an IPv6 application control IM message with level - information
generating deep application control logs with level - information
generating an antispam message with level - notification
generating an allowed traffic message with level - notice
generating a multicast traffic message with level - notice
generating a ipv6 traffic message with level - notice
generating a wanopt traffic log message with level - notification
generating a HA event message with level - warning
generating a VOIP event message with level - information
generating authentication event messages
generating a Forticlient message with level - information
generating a URL block message with level - warning
generating a DNS message with level - warning
generating an ssh-command pass log with level - notification
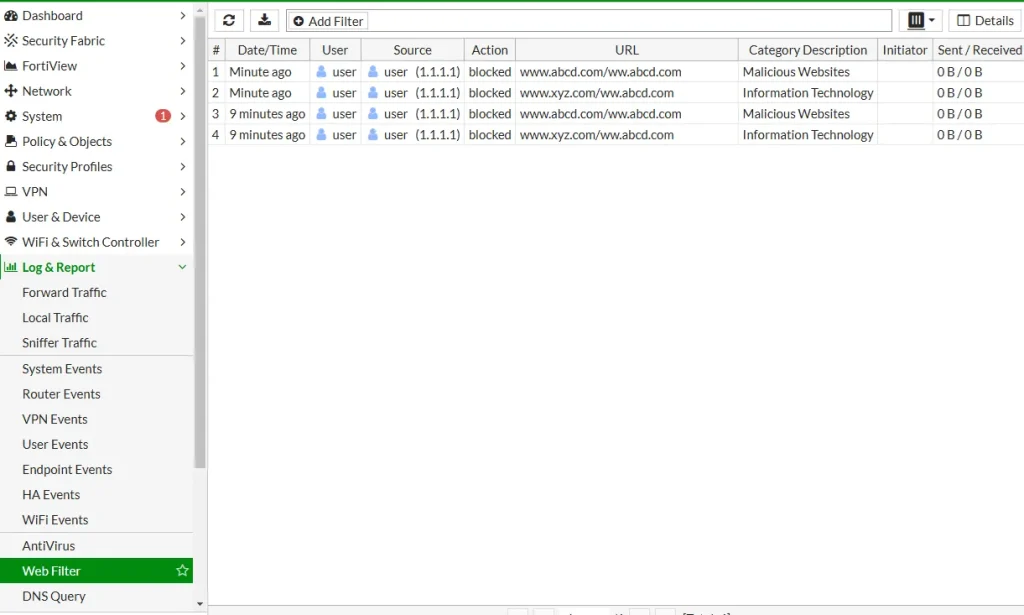
generating an ssh-channel block with level - warningCheck the logs under Log & Report -> Web Filter
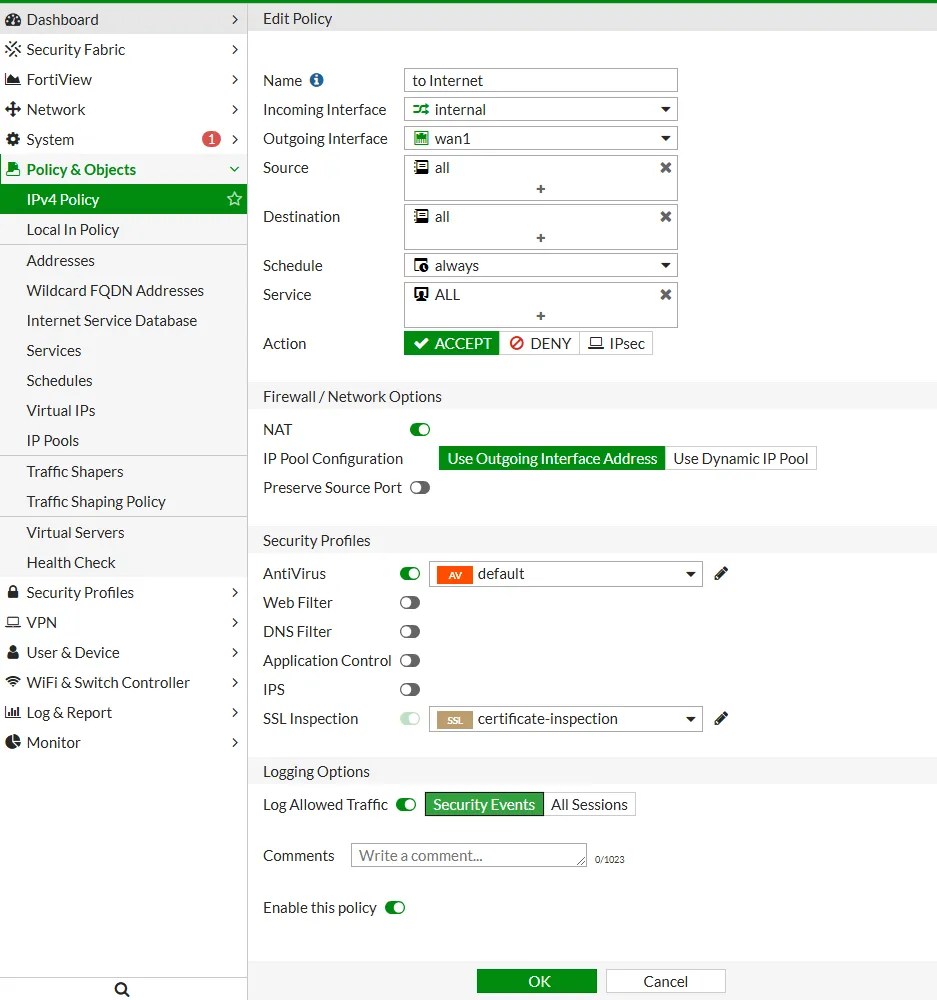
Enable Logging in Firewall Policy
If you configure your FortiGate to inspect traffix you should enable logging for that security feature to track and debug your traffic flow.
You can enable logging in firewall policies on this way:
- Enable security profile or all of them
- Enable Log Allowed Traffic: Security Events or All Sessions
- In my case I enabled just “Security Events”
Protecting Log Data
Ensuring log integrity is critical for security and compliance:
- Enable encryption for remote log transmission.
- Use access controls to restrict log viewing.
- Implement redundancy by storing logs in multiple locations.
- Regularly back up logs to prevent data loss.
By following best practices and leveraging FortiGate’s robust logging capabilities, administrators can gain valuable insights into their network, improve security, and ensure regulatory compliance.
You can check my aritcle related to the Fortient FortiGate: Network Monitoring with Custom Dashboards to discover more about logging.













