OpenVPN Client Failover Script
Failover mechanisms play a crucial role in maintaining continuous connectivity between remote sites. In small office environments, branch offices, and industrial deployments with IoT devices, OpenVPN provides secure tunnels for data exchange. However, when the VPN tunnel drops, these systems lose connectivity unless you act quickly.
This is where automated failover and notification mechanisms come in. With simple MikroTik scripting, you can detect OpenVPN tunnel failures, switch to a backup route or connection, and receive notifications the moment a problem appears.
Problem Overview
MikroTik does not offer built-in automatic failover or notification when an OpenVPN tunnel drops. This limitation becomes critical in environments where stable VPN connectivity ensures remote access, site-to-site operations, or IoT command channels. Without automation, downtime goes unnoticed until users or services begin to fail.
Solution for Failover – Tunnel Status Failover Script
MikroTik’s scripting engine gives you enough control to detect when an OpenVPN tunnel goes down and trigger a failover.
How the Script Works
The failover script automatically monitors the status of multiple OpenVPN client interfaces and ensures that at least one tunnel remains active. The logic follows a linear priority-based approach:
- Interface Definitions
The script defines three OpenVPN clients in order of priority:openvpn_client_1– primary VPN tunnelopenvpn_client_2– secondary (backup) VPN tunnelopenvpn_client_3– tertiary (last-resort) VPN tunnel
These names must match the actual interface names on your MikroTik router.
- Status Check
The script loops through all OpenVPN client interfaces and checks which one is currently running (connected). It stores the name of the active tunnel in a variable. - Failover Conditions
- If
openvpn_client_1is enabled but not running, the script disables it and enablesopenvpn_client_2. - If
openvpn_client_2is enabled but not running, it disablesopenvpn_client_2and enablesopenvpn_client_3. - If none of the tunnels are running (no active VPN client detected), the script reverts to
openvpn_client_1as the default and disablesopenvpn_client_3to reset the state.
- If
- Action Logging
All tunnel switches are logged using the:log infocommand so that administrators can review failover events in the MikroTik system log. - Scheduled Execution
The script is intended to run at regular intervals (e.g., every 1 minute) using the system scheduler. This ensures real-time detection and correction of tunnel failures without manual intervention.
This logic ensures that the router always has an active route to the internet or remote location, even when the VPN fails.
Script Code
Save the script under the name vpn-failover-script.
# Define the OpenVPN client interface names
# IMPORTANT: Adjust these interface names to match your own configuration
:local openvpn_client_1 "openvpn_client_1"
:local openvpn_client_2 "openvpn_client_2"
:local openvpn_client_3 "openvpn_client_3"
# This variable will hold the name of the currently active OpenVPN client
:local activeClient ""
# Check all OpenVPN clients to find which one is currently running
:foreach i in=[/interface ovpn-client find] do={
:local clientName [/interface ovpn-client get $i name]
:local clientStatus [/interface ovpn-client get $i running]
:if ($clientStatus = true) do={
:set activeClient $clientName
}
}
# Check if openvpn_client_1 is enabled but not running
:if ([/interface ovpn-client get [find name=$openvpn_client_1] disabled] = false && [/interface ovpn-client get [find name=$openvpn_client_1] running] = false) do={
:log info ("openvpn_client_1 is enabled but not running. Disabling openvpn_client_1 and enabling openvpn_client_2.")
/interface ovpn-client disable [find name=$openvpn_client_1]
/interface ovpn-client enable [find name=$openvpn_client_2]
} else={
# Check if openvpn_client_2 is enabled but not running
:if ([/interface ovpn-client get [find name=$openvpn_client_2] disabled] = false && [/interface ovpn-client get [find name=$openvpn_client_2] running] = false) do={
:log info ("openvpn_client_2 is enabled but not running. Disabling openvpn_client_2 and enabling openvpn_client_3.")
/interface ovpn-client disable [find name=$openvpn_client_2]
/interface ovpn-client enable [find name=$openvpn_client_3]
} else={
# If none are running, enable openvpn_client_1 as default
:if ($activeClient = "") do={
:log info "No active OpenVPN clients found. Enabling openvpn_client_1 and disabling openvpn_client_3."
/interface ovpn-client disable [find name=$openvpn_client_3]
/interface ovpn-client enable [find name=$openvpn_client_1]
}
}
}Notes for the Readers
- Adjustable Parameters: You must change the values of
openvpn_client_1,openvpn_client_2, andopenvpn_client_3to match the names of your OpenVPN client interfaces. These are defined at the top of the script. - Failover Logic:
- If client 1 fails (enabled but not running), switch to client 2.
- If client 2 fails, switch to client 3.
- If no clients are running, re-enable client 1 as a fallback.
- Logging: The script logs each action for easier troubleshooting. You can view these logs under Log > Info in Winbox or WebFig.
Script Implementation
Step 1: Find OpenVPN Connections which will be Part of the Script

Step 2: Copy Script to Mikrotik Router
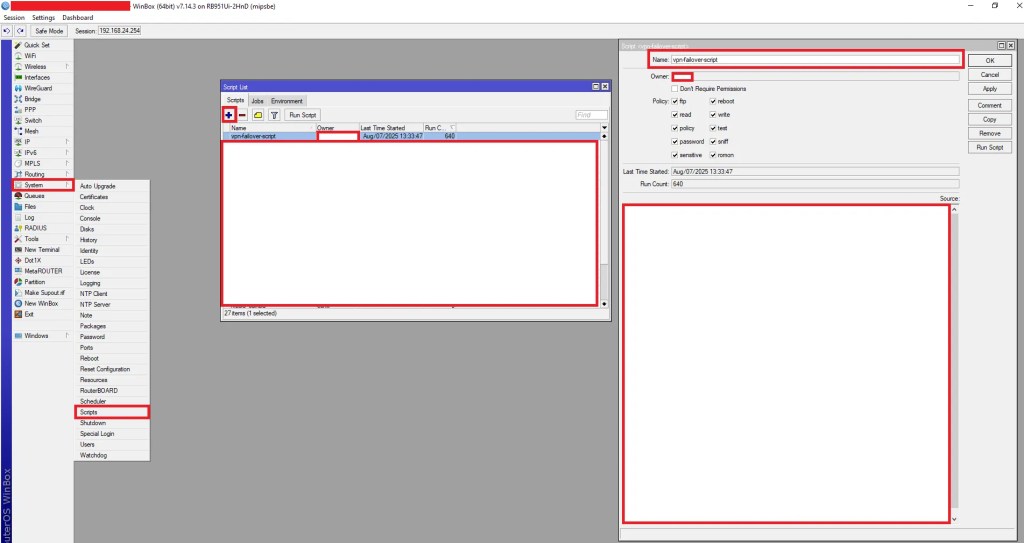
- Go to System > Scripts.
- Create a new script and paste the code.
- Script name: vpn-failover-script
Step 3: Create a Scheduler
- Open System > Scheduler, add a new entry:
- Interval: 00:00:30
- On Event:
/system script run vpn-failober-script
- Make sure you test the VPN drop and failover route before putting it into production.

Conclusion
This failover script enhances the reliability of your MikroTik VPN setup by automatically reacting to tunnel failures. It ensures your remote sites or services stay connected, even when the primary VPN link drops. Combined with a monitoring or notification system (covered in the next post), it becomes a powerful high-availability solution.
Combined with a proper OpenVPN setup and a reliable backend VPN server like SoftEther, this failover script ensures your remote access remains stable and automated.
If you haven’t set up your tunnel yet, follow this OpenVPN configuration guide for MikroTik.
For advanced setups, consider running a SoftEther VPN server as the remote endpoint.













