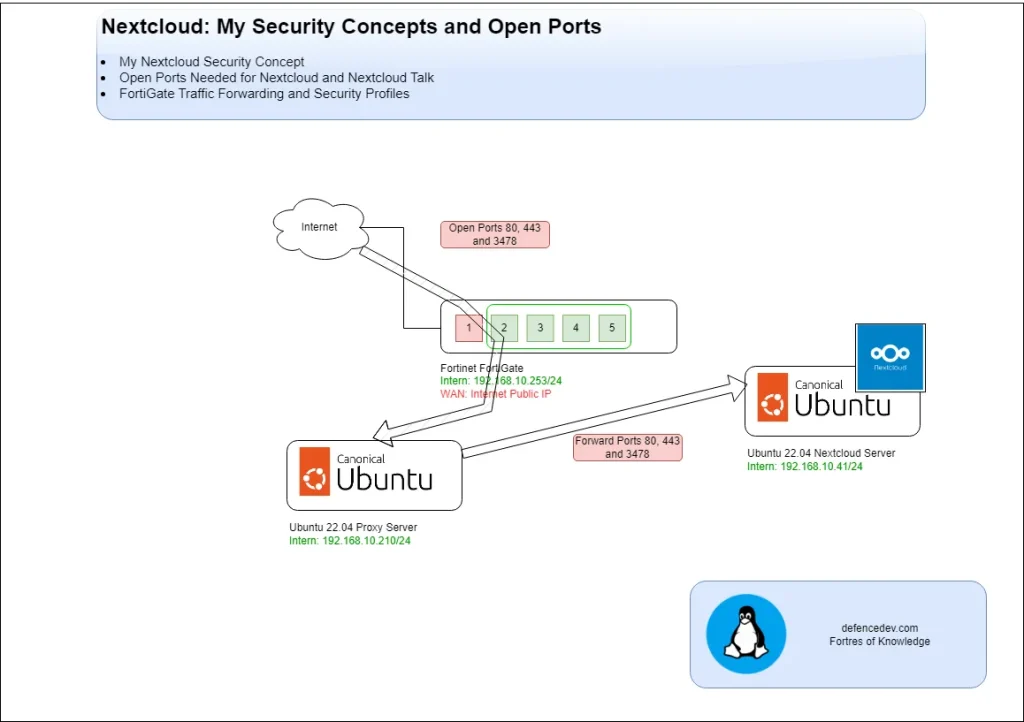
Nextcloud Access with Multiple Domains
You want to access your Nextcloud server using two domain names:
data.defencedev.com(main)newdata.defencedev.com(secondary)
Nextcloud is hosted on a local machine (e.g., 192.168.10.41).
You either use:
- A reverse proxy like Nginx Proxy Manager
or - Direct port forwarding from your router to the Nextcloud host.
But you encounter redirect or SSL errors, especially when using both domains.
Error Example:
Misdirected Request
The client needs a new connection for this request as the requested host name does not match the Server Name Indication (SNI) in use for this connection.
Apache/2.4.52 (Ubuntu) Server at data.defencedev.com Port 443Issue in the Configuration for Multiple Domains
In my case, you added the HTTP port redirect rule to the 000-default.conf file in Apache like this:
root@nextcloud:/etc/apache2/sites-enabled# ls
000-default.conf
data.defencedev.com-ssl.conf
newdatadata.defencedev.com-le-ssl.conf
RewriteEngine on
RewriteCond %{SERVER_NAME} =newdata.defencedev.com [OR]
RewriteCond %{SERVER_NAME} =data.defencedev.com
RewriteRule ^ https://%{SERVER_NAME}%{REQUEST_URI} [END,NE,R=permanent]After this, your site became inaccessible.
Misdirected Request Why?
This rewrite interferes with SSL offloading handled by the Nginx Proxy Manager, which terminates HTTPS and sends traffic to Apache over HTTP (port 80).
Option 1: Access via Nginx Proxy Manager
1. Apache HTTP Configuration (80)
Disable redirect rules! Your Apache should only serve content and leave SSL to the proxy.
Example /etc/apache2/sites-enabled/000-default.conf:
<VirtualHost *:80>
ServerName data.defencedev.com
ServerAlias newdata.defencedev.com
DocumentRoot /var/www/html
<Directory /var/www/html>
Require all granted
AllowOverride All
Options FollowSymLinks
</Directory>
</VirtualHost>
⚠️ No HTTPS config needed in Apache when using Nginx Proxy Manager.
While configuring your redirect rules (like the one in 000-default.conf for HTTP), it’s equally important to think about security and long-term usability. I’ve written more on these topics:
2. Nextcloud Configuration
Edit /var/www/html/config/config.php:
'trusted_domains' =>
array (
0 => '192.168.10.41',
1 => 'data.defencedev.com',
2 => 'newdata.defencedev.com',
),
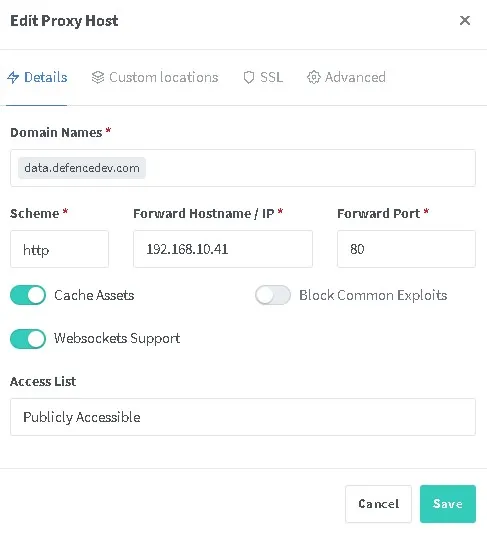
3. Proxy Manager Configuration
If you use NGINX Proxy Manager, you can easily manage multiple domains and SSL certificates via a user-friendly web interface.
In our case, we want to access the same Nextcloud instance via two domains:
data.defencedev.com(primary)newdata.defencedev.com(secondary)
The proxy forwards external HTTPS requests to the internal HTTP port of the Nextcloud server:
data.defencedev.com (HTTPS) → 192.168.10.41 (HTTP, port 80)
newdata.defencedev.com (HTTPS) → 192.168.10.41 (HTTP, port 80)You only need to issue and renew certificates from within the Proxy Manager. Your internal server doesn’t need to handle SSL at all.
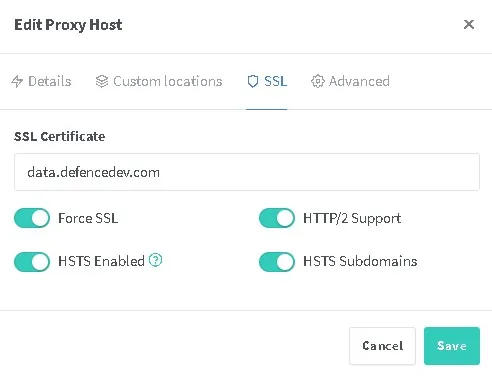
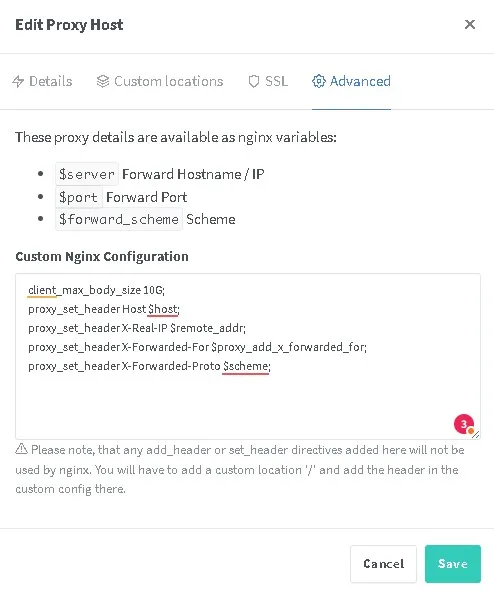
Content of the Advanced Settings
client_max_body_size 10G;
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;Be sure that both domains are added in the Nextcloud config (trusted_domains) and that the proxy settings are correct. For details on installing NGINX Proxy Manager on Raspberry Pi, see the step-by-step guide here:
Certificates are renewed only on the Proxy Manager.
Option 2: Access via Direct Port Forwarding
If you’re not using a proxy, and forward ports 80 & 443 directly from router to Nextcloud:
1. Apache HTTP (80) + HTTPS (443) Configuration
HTTP config /etc/apache2/sites-enabled/000-default.conf:
<VirtualHost *:80>
ServerName data.defencedev.com
ServerAlias newdata.defencedev.com
Redirect permanent / https://data.defencedev.com/
</VirtualHost>
HTTPS config /etc/apache2/sites-enabled/data.defencedev.com-ssl.conf:
<VirtualHost *:443>
ServerName data.defencedev.com
ServerAlias newdata.defencedev.com
DocumentRoot /var/www/html
SSLEngine on
SSLCertificateFile /etc/letsencrypt/live/data.defencedev.com/fullchain.pem
SSLCertificateKeyFile /etc/letsencrypt/live/data.defencedev.com/privkey.pem
<Directory /var/www/html>
Require all granted
AllowOverride All
Options FollowSymLinks
</Directory>
</VirtualHost>✅ Use
certbotor another tool to manage SSL certs on this server.
2. Nextcloud Configuration
Edit /var/www/html/config/config.php:
'trusted_domains' =>
array (
0 => 'data.defencedev.com',
1 => 'newdata.defencedev.com',
),
Conclusion
- If using a reverse proxy, avoid using
RewriteRulesor enabling SSL in Apache. - Let the Proxy Manager handle HTTPS and certificates.
- If using direct access, configure both HTTP and HTTPS in Apache, and make sure to properly redirect to HTTPS.
- In all cases, make sure your Nextcloud config lists all trusted domains.
Related posts you might find useful
If you’re interested in improving your Nextcloud setup even further, check out some of my related articles:
- Top 5 Must-Have Nextcloud Apps – Boost productivity and functionality with these essential apps.
- My 2-Year Experience with Nextcloud – Lessons learned and practical tips from long-term, real-world use.