Protect Docker-Hosted Application
Protect Docker-Hosted applications and Raspberry Pi infrastructure which hosts multiple Docker applications, from different types of DDoS attacks is abig challange. After many tests, logs, and stress scenarios, I finally decided to write a custom Bash script that does the job for me. ????
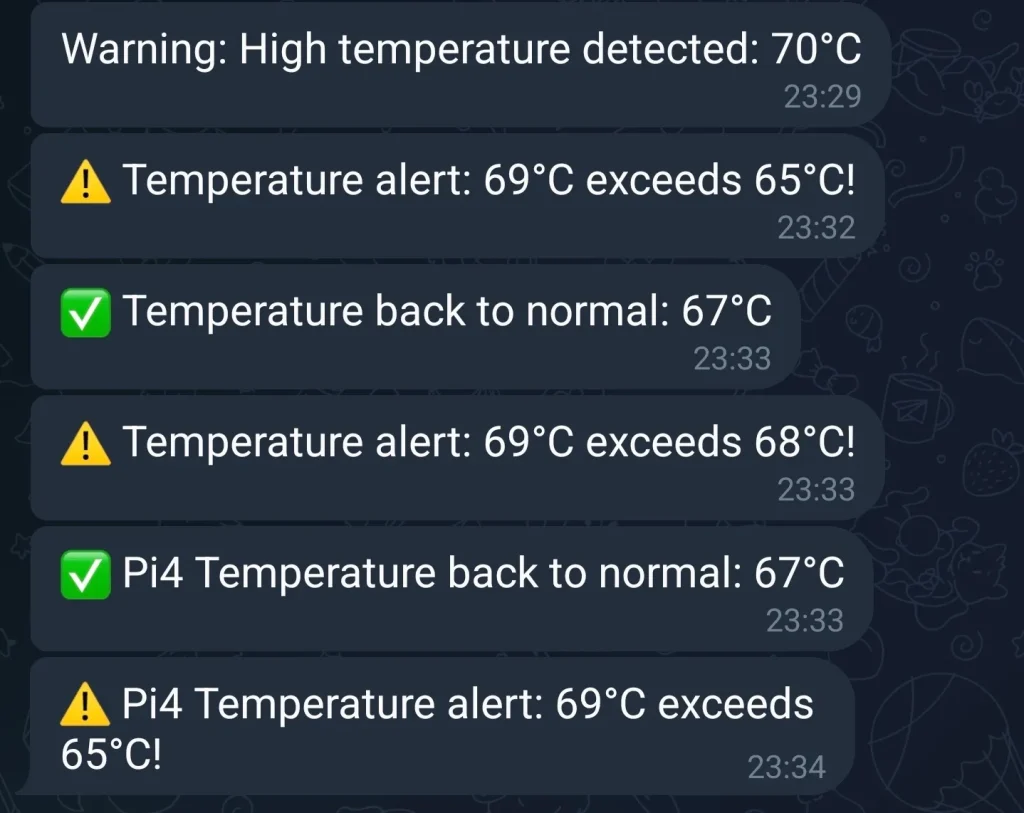
My network includes several Raspberry Pi devices, each running its own set of services. These devices are small, but sensitive. When they receive too many HTTP requests in a short time, the temperature rises quickly, which can cause system reboots—or even hardware failure.
To prevent that, I already have an efficient protection system on my FortiGate firewall. But I needed something more. I wanted per-device traffic control—to know exactly which Raspberry Pi or Docker service is under pressure.
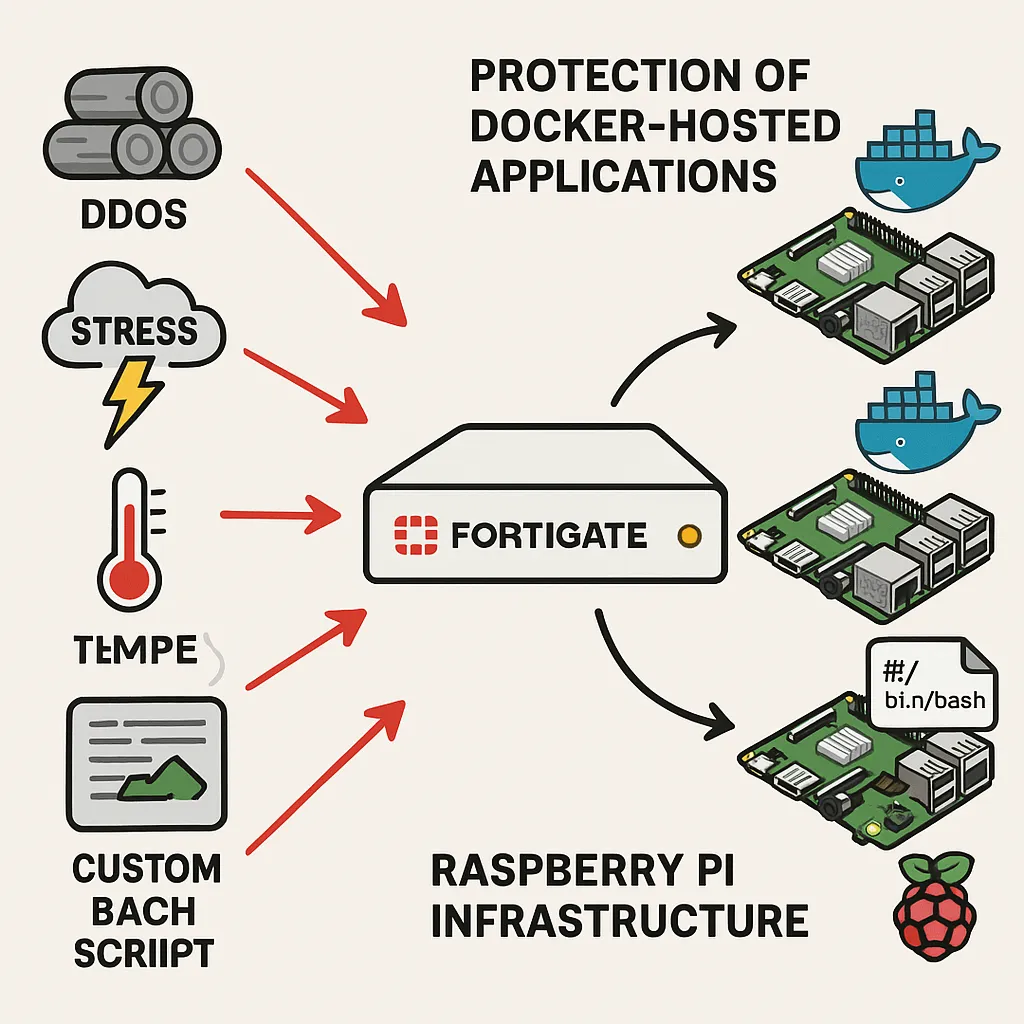
So I added an additional protection layer directly on each Raspberry Pi using a smart, lightweight Bash script.
In this article, I’ll show you exactly how it works—and the results it gives.
Common DDoS Attacks on Infrastructure and Docker-Hosted Applications
Web servers and backend infrastructure are constantly targeted by automated scanners and malicious bots. Here are some of the most common attacks:
- HTTP Flood (Layer 7 DDoS): Sends thousands of seemingly legitimate requests to overload the web server and exhaust its resources.
- Port Scanning: Identifies open services and exploits misconfigured or outdated software.
- Brute Force Attacks: Repeatedly tries to guess login credentials on admin panels, FTP, SSH, or CMS platforms like WordPress.
- SQL Injection: Injects malicious SQL queries via forms or URLs to access or destroy your database.
- Cross-Site Scripting (XSS): Injects scripts into web pages that execute in the browser of unsuspecting users.
- Exploiting Vulnerable Plugins or CMS: Especially common on platforms like WordPress, Joomla, or Drupal.
- Zero-Day Attacks: Exploits newly discovered vulnerabilities before patches are released.
- Bot Crawling and Scraping: Consumes resources while attempting to harvest your content, structure, or price data.
These attacks can slow down your services, overload the CPU or memory, and even expose sensitive data. That’s why proactive monitoring and protection are essential—especially when running lightweight hardware like Raspberry Pi.
How HTTP Flood DDoS Attacks Work
An HTTP flood attack sends an overwhelming number of requests to your website in a short period of time. It doesn’t rely on malformed packets or protocol exploits. It’s a legitimate-looking storm of GET and POST requests.
The attacker doesn’t need advanced tools—just a script or botnet that hammers your server.
This causes high CPU usage, memory overload, and your site either slows down or stops responding.
Protect Docker Application – Detection Idea: Count Requests per IP
My idea was simple:
If a single IP sends too many requests in a short time, block it.
I decided to monitor the Docker container logs, extract client IPs, and count how many times they appear within a defined window (like 60 seconds).
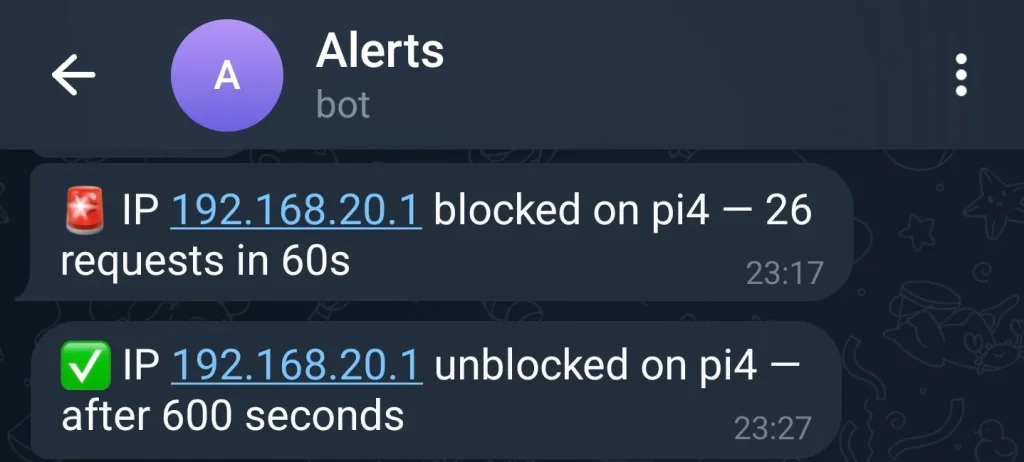
If that number exceeds a set threshold (e.g. 20 requests), I block the IP temporarily using iptables.
I also use an allowlist to make sure trusted IP addresses are never blocked.
And just to be sure I’m always in the loop—I added Telegram alerts.
The Bash Script That Does It All
Here’s what the script does:
- Reads Docker logs from a specific container.
- Extracts IP addresses from access logs.
- Counts how many times each IP appears.
- Compares against a defined threshold.
- Checks an allowlist of trusted IPs.
- Blocks suspicious IPs using
iptables. - Unblocks them after 10 minutes.
- Logs everything per day.
- Sends a Telegram alert when an IP is blocked or unblocked.
Full script will be available on my GitHub account.
Conclusion
Just a few lines of Bash can give you real-time DDoS defense, with full control and transparency.
This solution has helped me keep my Docker-hosted WordPress site responsive and protected—even during automated scan attempts and high traffic bursts.